Why IoT matters in physical security
Wondering what the difference is between IoT and IIoT and why they matter? Get these answers and learn how cloud, cybersecurity, unification, and AI impact the success of your network infrastructure.

IoT, or the Internet of Things, refers to the vast network of connected devices that gather and share data. It’s reshaping how we connect, monitor, and optimize systems. Did you know that there will be a projected 30 billion Internet of Things (IoT) devices in use by 2030? That’s nearly a threefold increase from the IoT devices installed in 2020. And this is a conservative estimate, others in the industry believe it could happen sooner.
You might have also heard about the industrial Internet of Things (IIoT). IIoT is a subcategory of IoT, focusing specifically on industrial and enterprise applications. It goes beyond consumer devices—connecting sensors, equipment, and systems within businesses. The result? Streamlined physical security, operations, and infrastructure management. Precedence Research says the global IIoT market will reach a value of $1.74 trillion USD by 2030. That’s a compound annual growth rate of 20.47% from 2022 to 2030.
Discover the top trends that are making it easier and safer to bring all your data together and generate meaningful outcomes below.
FEATURE NOTE
What is IoT? What does IoT mean?
The Internet of Things, or IoT for short, represents the convergence of various sensors, devices, software, applications, and other technologies that connect and exchange data with each other over the internet or other networks.
IoT is a networked ecosystem of physical objects that are embedded with capabilities to communicate, sense, and interact with other connected technologies in the environment.
What’s the difference between IoT and IIoT?
IoT generally relates to connecting various network devices to the internet. These can be either consumer-based IoT devices or industrial. It’s a broad concept that covers many different types of connected devices. But how is this different from IIoT?
Here’s an easier way of looking at it:
- Consumer IoT: This category includes devices like smart speakers, wearables, home automation systems, and smart lights. They make everyday life easier and enhance user experiences.
- Industrial IoT (IIoT): This subcategory of IoT applies to industrial settings. The focus is on device connectivity across a business to boost efficiency. This includes connecting sensors, monitoring tools, and other industrial devices to improve operations. It often uses standard protocols like BACnet and SNMP to maintain reliable connectivity for industrial processes.
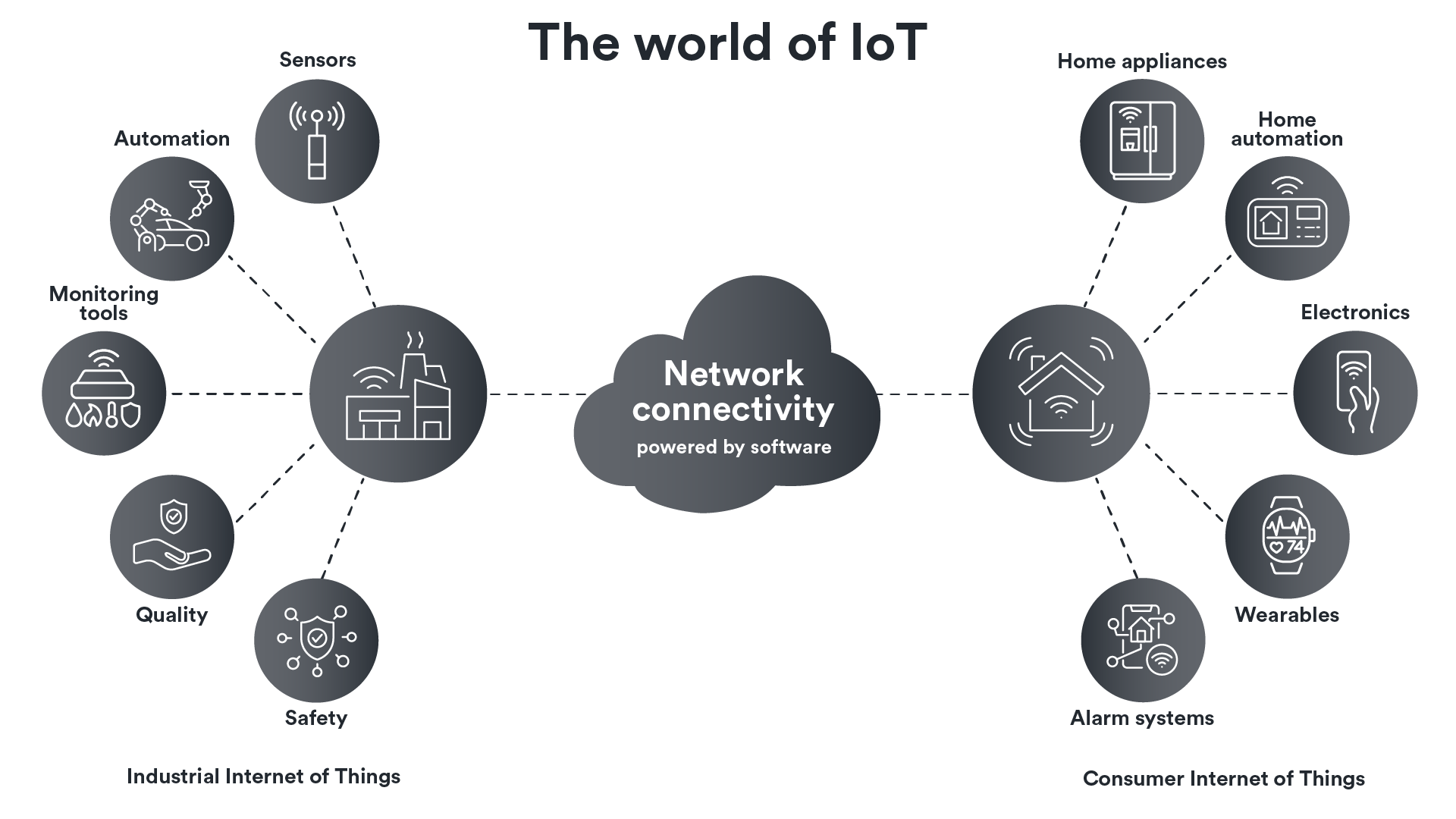
In this blog post, we’ll be focusing the discussion on IIoT and how connected systems and devices are benefitting businesses.
Today, many organizations are implementing IIoT strategies to achieve specific business outcomes. For example, some businesses are merging video surveillance and access control systems with lighting and HVAC solutions to enhance automation, reduce energy consumption, and meet sustainability mandates. They’re looking closely at building management systems and building automation.
BLOG
What is Industry 4.0?
Industry 4.0 represents a new phase in the industrial revolution. It’s driven by increased interconnectivity and automation, with IIoT and smart manufacturing leading the way forward.
Here’s a quick breakdown of where this fits in the broader landscape:
- Industry 3.0: Also known as the digital revolution. This era introduced computers and automation, moving away from mechanical systems to digital electronics. It’s a move that brought huge improvements to production processes and business operations.
- Industry 4.0: The next phase integrates IIoT, automation, and connected systems. Industry 4.0 is known for its use of sensors, monitoring tools, and connected devices. This helps improve operations and make more informed decisions by giving businesses a holistic view of their organization.
- Industry 5.0: Now emerging, Industry 5.0 goes a step further by prioritizing increased collaboration between humans and machines. It’s no longer ‘us vs. them.’ Instead, the use of artificial intelligence and learning models can add more adaptability and precision to processes and physical security. Machines are in no way ready to take over. They are, however, becoming an important tool to help keep people safe.

Organizations today are adopting Industry 4.0 principles into their security, services, and daily operations. While these initiatives are becoming more prevalent now, forward-thinking businesses have long understood the value of connecting IIoT devices. It’s how they discover new ways to become more resilient, improve processes, and enhance customer experiences.
BLOG
How the cloud and other key trends move IIoT forward
IIoT adoption has steadily increased, motivated by the growing need for greater versatility. With hybrid work becoming a new normal, organizations have had to adapt quickly. This means enabling secure access to critical applications and data from anywhere. For many, the way forward is the way of flexibility. Employees across the globe now have the option of choosing whether they want to work on-site, remotely, or somewhere in between. All while businesses keep things running efficiently and smoothly using IIoT devices.
Meanwhile, advancements in cloud infrastructure and connectivity protocols have paved the way for more widespread IIoT initiatives. More specifically, faster and more efficient data transfer. Organizations have the ability to gather granular information across long distances. Cloud applications also bring powerful computing, data processing, and storage capabilities. These benefits provide a scalable path to expanding existing systems, launching new applications, and sharing data across different locations.
The cloud continues to broaden opportunities for businesses that want greater connectivity across their Industrial Internet of Things devices. And there’s so much more flexibility in deploying new solutions while bringing all their existing investments into the IIoT environment.
For example, new cloud-connected infrastructure appliances support the ability to have a hybrid-cloud architecture. This means IT and physical security professionals can upgrade their security infrastructure and expand connectivity to various devices, data, and locations, all while keeping existing sensors.
So, where existing equipment may have held organizations back from launching new IIoT strategies, these plug-and-play cloud appliances are bridging the gap for upgrades. Today, cloud solutions are making it simpler, more affordable, and even more secure to bring systems and data together, and make all of it accessible from any location.
Is cloud the best way to reinforce IIoT cybersecurity?
One of the biggest concerns for organizations is IIoT cybersecurity. Strong cybersecurity is essential with IIoT systems because as the number of connected devices increases, so do the risks for cyberattacks and data breaches. There’s no question that an organization’s main goal is to extract as much value from all the connected sensors. But the most successful outcomes also depend on how well they can build and maintain strong cybersecurity and data privacy.
Though the cloud is a main catalyst in IIoT, the long-held belief that the cloud isn’t secure simply isn’t true. In today’s world, keeping systems safe from threats is costly and complex. Usually, it requires dedicated resources, large budgets, and relentless diligence. With the right cloud solution, organizations can get many built-in cybersecurity features and tools that help automate processes and stay ahead of threats.
BLOG

How unification and analytics help make sense of the data
Connecting hundreds or even thousands of sensors in your environment can only benefit your team if they have the tools to make sense of the data coming in. This is why investing in an open architecture platform is critical. With an open and unified platform, you can bring data from various types of sensors and systems into one single solution. This creates a solid foundation on which you can keep expanding your IIoT initiatives.
For instance, you might start by combining your video, access control, and intrusion systems into one platform. Doing this will provide your security personnel with a clearer picture of events and enable them to quickly respond to threats and incidents within the environment.
From there, you might bring in other business systems such as intercom, building management, point-of-sale, or automatic license plate recognition. Having all these sensors drive data into one single platform gives your team a better understanding of what’s happening across your business. You’ll also be able to achieve higher levels of automation by setting up event-to-actions, scheduling weekly and daily reports, or using built-in APIs to build custom applications.
Think this sounds too good to be true? Below are five examples of how businesses today are making use of their data:
 |
Automating HVAC airflow in airports based on crowd levels |
Airports welcome millions of passengers through their facilities every day. And depending on daily flight schedules, crowds can form quickly in certain areas. Ensuring proper airflow throughout the airport is critical, especially when lots of people are condensed in security lines, at gates, or in specific terminal wings. The challenge is that running HVAC systems at full throttle all the time isn’t cost or energy efficient.
At an airport in Canada, the operations team was able to leverage video surveillance and crowd estimation analytics to better control airflow in various areas throughout the airport. For example, if their unified security platform detected a crowd forming in a specific area, the system would trigger the HVAC airflow in that zone to increase. When the crowd would subside, so would the airflow. This has not only helped to reduce energy costs and keep sustainability practices in check, but they’re also ensuring better quality air for their passengers during busier travel times.
 |
Using sound detection in restrooms to maintain safety and operations |
Video surveillance is very helpful to detect threats across university campuses, schools, or offices. But for obvious reasons, cameras cannot be installed in sensitive areas such as bathrooms. Some schools have found that implementing sound detection in bathrooms solves that problem.
For example, sound detection IIoT devices can detect certain keywords such as ‘help’. Within the unified platform, this would alert operators to a possible incident. They could then dispatch security personnel to check in on the situation. Janitors completing cleaning rounds in bathrooms can also say ‘cleaning done’. The unified platform would then log the completion of cleaning, digitizing janitorial processes.
 |
Detecting illegal dumping across a city |
Cities often have trouble managing illegal dumping activities. It’s difficult to detect the actual dumping incident and even harder to deter or identify suspects. Recently, the City of New Orleans (NOLA) took an innovative approach to address illegal dumping. NOLA’s Sanitation Department and Real-Time Crime Center worked in partnership to install cameras at known dumping sites, but the cameras alone weren’t enough.
The team also set up an event-to-action rule in the Security Center platform which processes motion detection in a defined zone of the camera’s field of view, and then immediately takes a snapshot of the video and emails it to specific people. Within two days of setting this event-to-action up, NOLA was able to identify and arrest a repeat offender.
 |
Identifying temperatures in server rooms or hospital medicine rooms |
Many organizations are managing large server rooms which house critical systems and data. Keeping these server rooms cool ensures investments are protected and business runs as usual. Hospitals face similar requirements in keeping certain medication rooms cool to ensure critical drugs don’t spoil.
One way to track temperatures for these specific applications is by installing air temperature sensors in these rooms. So, if a cooling system fails and temperatures begin rising or even reach a specific threshold, your team will be immediately alerted.
Sometimes, this might have nothing to do with an HVAC failure but because someone accidentally left a door propped open. This is where having all data unified within one platform comes into play. The system would be able to quickly detect, both the door ajar for too long and a rise in room temperature, and quickly identify that it's likely an urgent situation and push all that information to an operator. They can then investigate and remediate the situation. They can also quickly identify who was last in the room based on cardholder information, and follow up with additional protocols.
 |
Automating building controls to enhance sustainability efforts |
Building management systems and building automation are important components in IIoT. According to new sustainability research in physical security, 42% of organizations have their access control system linked to their building management system. Another 35% use the data from their access control system to drive greener operations.

For instance, customers can use standard protocols in Security Center to automatically activate heating, cooling, lighting, and other building functions at the tap of an access control card to a reader. So when the first employee enters the building or office using their mobile credentials or access card, the unified platform would trigger the heating or cooling to reach the desired temperature and the main lights to automatically turn on.
An automatic license plate recognition system can also be set up in the same way. So when the first vehicle is detected entering a parking lot, the building functions are activated.
Get insights from your IIoT sensors and system data
Organizations have so many IIoT devices in their environment, so it only makes sense that many are exploring new ways to leverage the data. But with cybersecurity top of mind and endless possibilities to offer, it’s not always easy to find the best path forward.
Working with a vendor that you can trust is critical. Not only will they offer your organization the tools to keep your data private and protected; but they can also help you assess your current environment, build a phased roadmap, and guide you through the process of achieving your IIoT objectives.
