How to maintain a strong cybersecurity strategy
Looking for tools to help you implement and maintain a strong cybersecurity strategy? Check out our blog post.

Did you know that cybercrime damages are predicted to cost the world $10.5 trillion annually by 2025?
That’s exponentially more than the damage inflicted from natural disasters in a year, and more profitable than the global trade of all major illegal drugs combined, according to the Cisco/Cybersecurity Ventures 2020 Cybersecurity Almanac.
To help you defend against cyberattacks, we shared 10 cybersecurity best practices in our last post.
Now, we’re going to cover some important tools and resources that you can use to maintain a strong cybersecurity strategy.
Work with built-in automation tools
Cybersecurity is only one of many challenges you’re overseeing every day. You can make your life easier by choosing solutions that help you automate maintenance and health monitoring to stay on top of possible vulnerabilities.
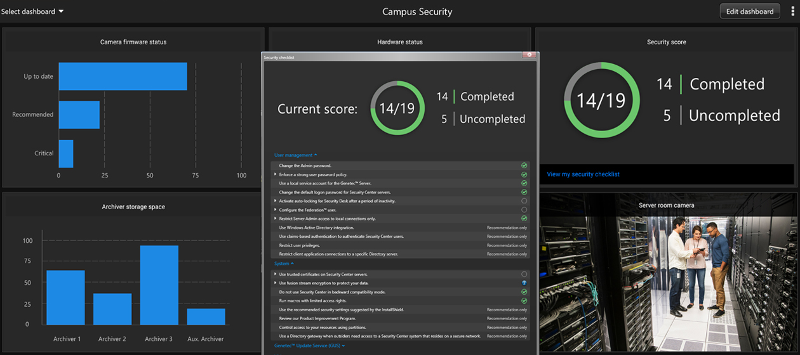
Instead of risking potentially faulty and incomplete self-assessments, a security platform developed with cybersecurity in mind can save you time and worry by telling you what’s happening and what needs to be done to comply with best practices. For example, here are some features that we have developed and shared with our customers:
The System Availability Monitor (SAM) works quietly in the background, monitoring the status and health of each individual component within your system. That means as soon as a camera goes offline, SAM lets you know about it.
The Genetec Update Service (GUS) alerts you to all the new product updates. That way if there are new features or fixes being released, you can automatically download updates in the background and install it on schedule or when time allows.
The new Security Score widget automatically tracks the security of your system in real-time and tells you clearly where you stand. It does this by laying out guidelines and then monitors whether the different elements of your system comply. All the information is available on one page, letting you know exactly what you need to do to improve your score.
Consider the perks of cloud solutions
Leading cloud services come with many of the built-in security mechanisms described above and even take it a step further. For instance, cloud services providers are responsible for handling system updates.
Top-tier cloud service providers also take responsibility for the risks and invest significant money and resources to strengthen their security. They deploy global incident response teams who work around the clock to mitigate cyber threats. They embed mandatory security requirements into every phase of the platform’s development and maintain unprecedented levels of security at their data centers.
Essentially, when you choose cloud services, you’re outsourcing a lot of the risks and costs associated with a good cybersecurity strategy to the provider.
Consult your vendors’ hardening guides
It can be difficult to keep track of all the different cybersecurity measures that are available to you. That’s why most leading security solution vendors will offer their customers hardening guides.
These guides provide specific recommendations on how to keep your system secure. Not only do they spread awareness of the threat landscape, but they also inform customers about the basic and advanced-level security features to minimize vulnerabilities and keep systems secure.
Choosing a trustworthy vendor
Maintaining a good cybersecurity strategy is an ongoing process and one you shouldn’t have to tackle alone. Up next, we’ll be sharing some important considerations to make when choosing a vendor that you can work with and trust.
In the meantime, check out our other tips on how to maintain a strong cybersecurity strategy.
Need more cybersecurity tips and tricks?
Check out our cyberhardening tips in our video series.