Zero trust strategies for physical security
Learn all about zero trust security and how you can extend best practices across your physical security deployment.

The 2024 State of Adoption Survey found that 63% of organizations worldwide have either fully or partially implemented a zero-trust strategy. And over half of them are doing so because it’s now considered an industry best practice. But what does zero trust mean? And how does zero trust security work?
Keep reading to find out more about the zero-trust approach to security and how to choose technology vendors that support these objectives.
GUIDE
Why is zero trust required today?
Most information technology (IT) and security operations (SecOps) teams will tell you that older network security models that were built on the idea that ‘inside means trust’ no longer work.
In the past few years, many have learned this lesson the hard way. Putting a digital barrier around assets doesn’t hold up in a modern environment anymore. This is because threat actors are inevitably finding new, sophisticated ways to penetrate perimeter defenses.
Insider threats are also becoming a bigger problem. In the IT and Security Convergence report, 31% of physical security professionals indicated that their organization was targeted by cybercriminals last year.
In recent years, there’s also been an explosion in remote work, cloud computing, and endpoint devices requiring access to applications from outside corporate networks. The reality is that clearly defined network perimeters no longer exist in our digitally connected world. For all these reasons, zero-trust strategies are becoming the go-to when trying to mitigate cyber risks.
What is zero trust?
Zero trust, also known as zero trust security and zero trust architecture, is a security framework built on the principle to never trust and always verify. This means that devices and individuals, whether inside the corporate network or not, should never be trusted by default.
Instead, trust is evaluated and verified on a per-transaction basis. Every interaction needs to be authenticated, authorized, and validated before being granted access to network applications and data. This is typically based on a mix of identity and other attributes such as geolocation, time and date, and other relevant security posture contexts.
Even after a device or individual is verified, access is only granted to a specific resource. Applying limited access or just-enough-access is a core principle of zero trust architecture. It further minimizes east-west, lateral movement across the network through resource segmentation.
With a zero-trust strategy, continuous verification is also a must. This ensures that if certain device or individual attributes change, access can be immediately revoked.

What are the main pillars of zero trust security?
Wondering how to design and deploy a zero-trust architecture? Follow these seven core pillars to achieve zero trust in your organization:
User identity |
Verify and validate user identity and attributes before granting them access to the applications or resources. Limit user access to only the specific data and resources they need to do their jobs, according to access policies. This typically involves using security tools such as identity and access management systems (IAM) and multiple forms of authentication and authorization.
Device |
Identify, validate, and authorize any device that’s trying to connect to enterprise resources to ensure trust. Limit data access to each device as needed. Maintain current inventories of all authorized endpoint devices and make sure all devices are fully compliant with cybersecurity best practices before implementation.
Application and workload |
Assume all applications, digital processes, and other IT resources are not implicitly trustworthy. Consider dynamic authorization and continuous validation to fortify all workloads. Apply robust and comprehensive cybersecurity measures to identify tampering, unusual behavior, or unauthorized access across workloads and applications.
Data |
Categorize data and apply targeted access control policies and security measures to safeguard against data breaches. Protect data in transit, in use, and at rest using layers of encryption and authorization. Carefully select data center storage locations and continuously monitor data processing to identify unusual activity or data leaks.
Network environment |
Implement micro-segmentation to restrict the spread of threats. Divide networks into smaller, containerized segments that can be closely controlled and monitored using granular security measures and policies. Isolate sensitive resources to minimize the chance of unauthorized access.
Automation and orchestration |
Centrally manage and enforce the entire zero trust strategy across the organization. Consider automation to validate and maintain that all security policies are configured and upheld in the same ways on the LAN, WAN, wireless WAN, and across data centers. Make sure all users, devices, and applications are subject to the same controls.
Visibility and analytics |
Make sure all zero trust security processes—whether micro-segmentation, authorization, encryption, application workloads, or data processing—are all continuously being monitored and managed. Using intelligent tools and analytics that automate threat detection, enhance enterprise-wide visibility, and deliver real-time notifications for faster risk mitigation.
BLOG
The importance of choosing partners who implement zero trust
A zero-trust approach shouldn’t be limited to your own organization. It should also extend across your entire supply chain ecosystem. This is why it’s critical to choose providers that prioritize having a zero-trust architecture as much as you do.
If you’re considering cloud or hybrid-cloud solutions, keep in mind how zero trust factors into the technology vendor’s operations and product design. By default, vendors should consider the data center network unsafe and implement protocols that support a zero trust strategy.
CHECKLIST
For instance, vendors can provide extensive micro-segmentation across resources alongside granular security controls and continuous authentication. This means separating network workloads into smaller segments to thoroughly monitor traffic across each segment and restrict the spread of lateral threats.
Another factor your vendor can consider is ensuring information is distributed across siloed, independent repositories. This eliminates the risks of attacks on a central data repository. All data that is transmitted and received can be fully encrypted and digitally signed so that the cloud service only has access to the minimum data required to perform that task.
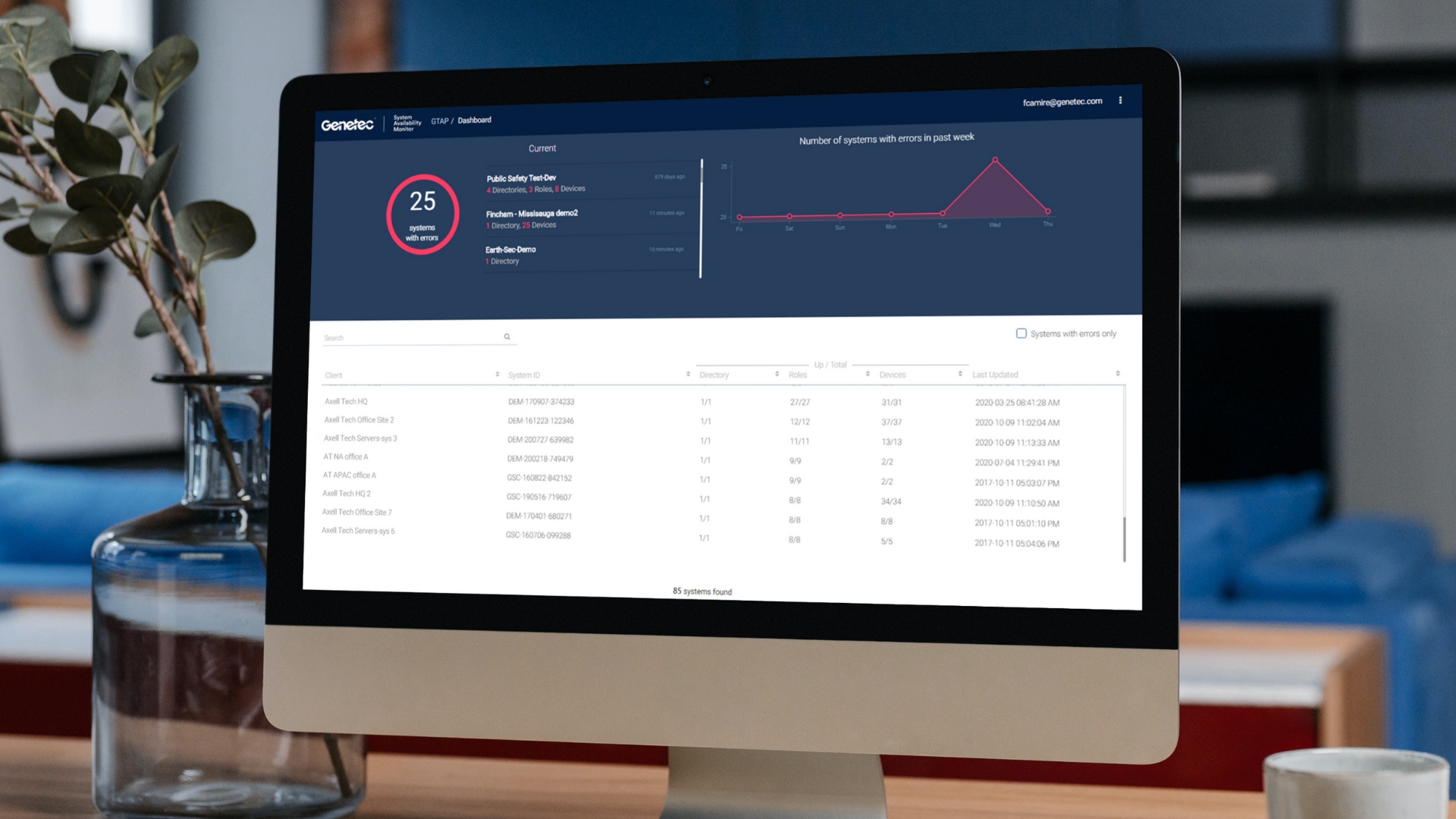
A cloud solution can come packed with health monitoring tools, automatically alerting you to vulnerabilities as they come up. This can include cybersecurity widgets that provide specific recommendations to enhance your cybersecurity posture.
Your due diligence can also include vetting the vendor’s compliance standards and certifications. It should involve checking whether their practices and solutions have been validated by third-party audits and accredited compliance associations. All of this helps to ensure that trust is warranted and continually re-assessed—a core principle of zero trust.
