How to strengthen the perimeter of electric utilities
What are the biggest threats to electric utilities? See how a simple 6-step plan can help you protect your perimeter and remain compliant with NERC rules.

Power grids aren’t just infrastructure — they’re the backbone of modern life. When they’re disrupted, everything from hospitals to water supplies to transportation is affected.
Global, attacks on power infrastructure are on the rise. From copper theft to cyberattacks, utilities are facing threats that are more frequent, more damaging, and harder to predict.
PORTFOLIO
Key challenges impacting electric utilities today
Theft and vandalism: Critical energy infrastructure is frequently targeted for theft of copper, fuel, and equipment, leading to operational disruptions and rising maintenance costs. Remote areas are particularly vulnerable.
Sabotage and organized attacks: In politically unstable or crime-affected regions, electric infrastructure is deliberately sabotaged, transmission systems are disabled, and maintenance crews are obstructed, threatening energy reliability.
Inadequate security measures: Many facilities lack proper fencing, surveillance, or trained security personnel, increasing risks of unauthorized access and physical intrusions, especially in rural and high-risk zones.

Copper theft isn’t going away
Let’s start with copper theft — a problem that’s been around for years, but still costs U.S. businesses close to $1.5 and $2 billion annually, according to the U.S. Department of Energy.
Why copper? It’s incredibly valuable, endlessly recyclable, and in high demand for everything from plumbing and EVs to fiber optics and solar panels. With prices hovering around $5 per pound, it’s no wonder people are risking their lives to steal it.
The consequences go beyond lost materials. On December 3, 2022, two Duke Energy substations in Moore County, North Carolina, were deliberately damaged, leaving approximately 40,000 customers without power. These incidents don’t just affect infrastructure — they put entire communities in the dark, sometimes for hours or even days. In some cases, outages like these can create life-threatening situations, especially for individuals who rely on powered medical equipment.
EBOOK
The rise of physical attacks
Copper theft is just one part of the problem. In recent years, we’ve seen a worrying trend: deliberate physical attacks on power infrastructure.
More recently, multiple substation attacks across the U.S. and Canada have triggered local outages and heightened security concerns. And it’s not just about vandalism — some incidents appear to be coordinated, suggesting a much deeper intent.
Across Latin America and Mexico, electric utilities are dealing with more break-ins, theft, and damage to their equipment. Substations and power lines are often hit by people stealing copper or fuel, and some attacks are planned by organized groups trying to disrupt service. Many of these sites are in remote areas with little security, making them easy targets.
Here’s what utilities are also up against:
- Sabotage of pipelines and terminals
- Wildfires and extreme weather taking out entire grid segments
- Insider threats from employees and contractors with authorized access
The bottom line? Physical threats are getting bolder — and more costly.
New infrastructure threats affecting the renewable energy sector
As more countries, including Australia, shift to clean energy, new types of infrastructure are being built and connected to the grid. This includes solar farms and battery storage sites, which are often in remote places. These sites can be just as at risk as traditional power plants, and sometimes even more so.
At the start of 2025, more than 40% of the electricity used in Australia’s main power grid came from renewable sources like solar farms and clean power stations. These systems often depend on long power lines to send electricity across the country, including from Queensland’s solar farms to other regions.
In one example, Australia’s CS Energy was targeted by a ransomware attack in 2022 that affected its corporate network. This shows how even renewable energy providers can face serious threats.
Why electric utilities face supply chain cyber risks
While physical risks are visible, cyber threats often hit without warning — and they can be just as destructive. Cyber attacks can happen at any point in the supply chain, and your physical security equipment is a potential entry point to your network and critical infrastructure. That’s why it’s crucial to select partners who have your network's best interests at heart. Choosing trustworthy vendors who prioritize security is vital in preventing potential breaches and minimizing risk.
Utilities are a growing target for cybercriminals and nation-state hackers. Why? Because modern power grids run on more than wires — they rely on digital systems, sensors, and software that can be hacked, spoofed, or shut down.
Here are some of the key cybersecurity challenges currently facing the energy and utilities sector:
- Hackers targeting operational tech (OT) and industrial control systems (ICS)
- Phishing attacks aimed at utility employees
- Unpatched software and vulnerable third-party vendors
- Internet of Things (IoT) devices that open backdoors
- And now, AI-powered attacks that can find and exploit weaknesses faster than ever
For utilities, it’s not about choosing between physical security and cybersecurity. It’s about doing both, and doing them well.
The threats to our energy systems are evolving, and so should our response. Whether it’s someone snipping copper wires or a hacker slipping through a digital crack, the impact can be huge.
Regulations designed to mitigate risk in electric utilities
North America has had a regulatory body working to protect the power grid since 1968. Today, that body is the North American Electric Reliability Corporation (NERC), a nonprofit organization whose mission is to ensure the reliability of the North American power system.
As part of its mandate, NERC has established a series of standards that enforce steps utilities can take to protect their environments and operations.
NERC’s systems approach to managing intruders
Instead of telling each utility exactly how to secure their stations, substations, and transfer stations, NERC offers an interpretative framework. Utilities are required to meet these enforceable standards and can tailor their compliance strategies to their specific systems and risks, often using a "defense-in-depth" approach. This method focuses on creating multiple layers of protection across large areas, rather than relying on a single strong defense.
Utilities are free to approach NERC compliance with their own strategies, as long as they abide by NERC CIP standards. It’s important to note that NERC can audit utilities at any time, and non-compliance can result in hefty fines of up to $1 million per day for each violation.
So, what does this approach involve?
It consists of six steps that utilities can implement based on their budgets and needs. The strategy includes various technologies to help prevent, discourage, or respond to unauthorized access at buildings, substations, and transfer stations. Utilities have the flexibility to decide how to best follow these steps.
GUIDE
6 steps to manage intruders in electric utilities
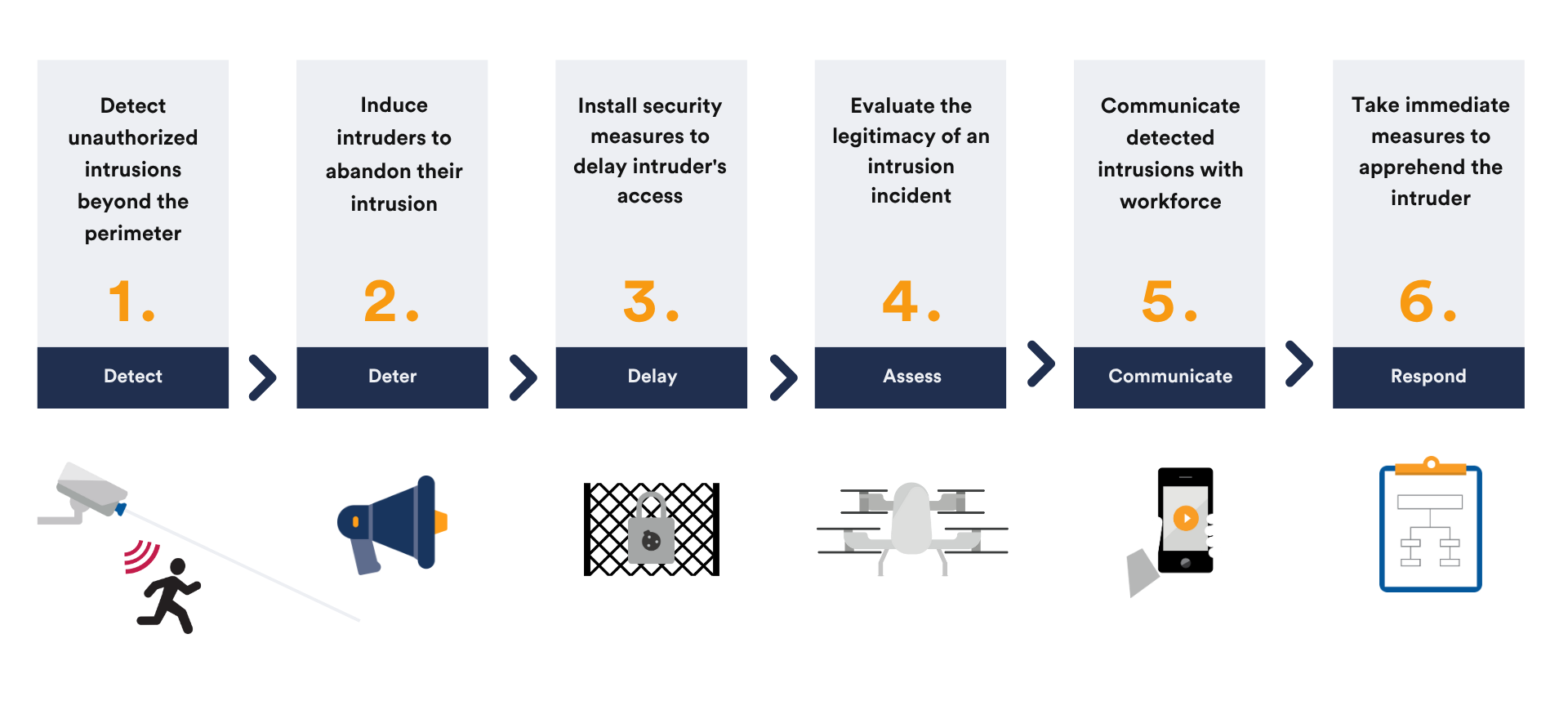
 Detect
Detect
The first step is to detect possible unauthorized intrusions beyond the perimeter. This can be done with a variety of sensors, thermal and video analytics, as well as a vehicle-centric investigation system which, which helps collect rich vehicle-based evidence and suspicious activity. One of the challenges associated with detection is that it can produce nuisance alarms. Your security platform should have a rules engine to correlate events and reduce nuisance alarms so operators are only notified of genuine threats.
 Deter
Deter
In this step, the goal is to deter unauthorized access to the utility using physical deterrents like lighting, walls, and fences, or by triggering actions from the security system. For example, it can activate strobe lights or play an MP3 on a loudspeaker. A public address system enhances this by broadcasting warnings, while a communications management system allows operators to coordinate swift responses in real-time.
 Delay
Delay
The goal here is to install security measures that delay physical access. This can include chain-link fences that are incredibly time-consuming to cut through. One of the benefits of this step is that it gives security personnel time to evaluate and properly respond to incidents.
 Assess
Assess
During this step, security operators evaluate the incident to determine what is happening and then identify the actions necessary to respond to the situation. Assessing an incident at a fence or other restricted area is much easier if security operators have “eyes on the scene.” This can include accessing nearby cameras or, in some cases, dispatching a drone to capture footage in real-time.
 Communicate
Communicate
For this step, utilities need to plan how security operators will communicate with each other. Command centers must be able to share information with mobile operators, who also need to exchange updates. A communications management system helps by ensuring smooth, real-time communication between everyone involved.
 Respond
Respond
Security operators need to take the appropriate measures to apprehend an intruder. This last step is made much easier, and frequently unnecessary when the earlier steps have been followed. But, if the situation requires that security operators take action, utilities need to ensure that they have established standard operating procedures that can help guide responses.

