Proprietary vs. non-proprietary access control systems
Learn about the differences between a proprietary and a non-proprietary access control system and how open architecture gives you the flexibility to adapt as your organization's needs change.

Whether you’re shopping for access control, video surveillance, or any other system, you may be asking yourself the following questions:
- What’s the difference between a proprietary and non-proprietary system?
- How does choosing a unified versus integrated solution compare?
- What’s the best type of system to support flexibility and continuous innovation?
Discover how proprietary and non-proprietary systems differ, how unified and integrated solutions offer you unique perks, and what the optimal solution is for long-term flexibility and investment longevity for your physical security system.
WHITE PAPER
What is a proprietary security system?
A proprietary system is designed with a closed architecture and implemented within a closed ecosystem by one vendor. That means you must purchase the hardware, software, support, and any other accessories or add-ons from the same technology provider.
Proprietary solutions offer no compatibility with solutions from other technology providers. In some cases, connections to other technologies are limited to what the vendor offers. This means that you’re fully locked into one vendor’s product and service portfolio. With a proprietary system, you’re also completely dependent on that one vendor to release new useful solutions, as well as to support your deployment over time.
How is a non-proprietary system different?
A non-proprietary system is engineered with an open architecture, meaning it’s designed at its core to work with compatible technologies from other providers. This allows you to connect non-proprietary software from one vendor with non-proprietary hardware and systems from other vendors, such as controllers, readers, or biometric technology.
This open ecosystem gives you the flexibility to design a system that meets your needs and requirements. And as your organization evolves and new technology comes to market, you’ll have the freedom to change things up or try out the latest innovations. Support is usually shared between vendors, and forward-thinking technology providers will collaborate to help you resolve any issues.
Knowing the difference between unified and integrated
Some physical security vendors will explain that system unification and system integration mean the same thing. Others believe that unification is exclusive to a non-proprietary system or requires a closed architecture. Both of these explanations are inaccurate.
Here are the facts:
- Proprietary and non-proprietary systems can be built as a unified solution by one vendor
- A non-proprietary, open architecture offers the broadest opportunity for integrations
- Unification and integration can co-exist and complement one another
Keeping this in mind, let’s dig into the difference between unification and integration:
Unification means that many different products have been engineered from the beginning to work together within a single solution. In physical security specifically, this can include access control, video surveillance, license plate recognition, intercoms, intrusion monitoring, and more. This type of system allows data to flow from multiple sources into one centralized view for a simpler operator experience. It also helps reduce time and costs associated with maintenance and training, since you can manage everything within one platform.
Integration is the ability to connect different products from different vendors, together. These products are typically engineered as stand-alone, but through SDKs and APIs, can be connected with other solutions. The depth of integrations can vary between solutions for various reasons. This can limit data sharing or system capability, making the experience a little less fluid between systems. Handling system or device maintenance may also become more tedious by having to log into different applications to handle certain tasks for various system components.
EBOOK
Here are a few things to remember:
A unified solution can be built on a closed architecture, meaning it’s proprietary and you only have access to the devices, systems, and services offered by the one technology vendor.
A unified system can also be built on an open architecture, meaning it’s non-proprietary. Beyond having access to systems and services from the technology vendor, you also can choose other compatible devices and solutions from a broad ecosystem of technology partners.
BLOG
Choosing between an open and closed access control system
Now that you understand all the terminology and how each compares within your deployment, let’s explore how this applies to your access control decision.
What’s a closed access control system?
A proprietary, or closed access control solution is provided by a single vendor. That means your door readers, controllers, access control software, and other access control devices or services, as well as support all come from one technology provider.
Some may say that proprietary solutions are more convenient since you’re only dealing with one provider, rather than with multiple vendors. However, a closed access control system limits the technologies you can choose for your deployment. If your vendor doesn’t keep pace with the latest innovations or stops supporting a legacy product, you’re stuck.
For these reasons, many organizations are moving towards modern, open architecture solutions. They want to gain more interoperability, freedom of choice, and scalability. They also want access to more advanced cybersecurity features. After all, emerging cyber and physical threats are putting legacy proprietary access control systems and their entire organizations at risk.
What’s an open access control system?
A non-proprietary, or open access control system means it’s been designed and engineered with an open architecture. This gives you the opportunity to choose access control software and hardware from different providers. Having this  flexibility allows you to make access control decisions that best serve your objectives and needs, all at your own pace.
flexibility allows you to make access control decisions that best serve your objectives and needs, all at your own pace.
You may also be able to reuse some existing hardware and wiring, saving a lot of time and money during an initial access control migration. And later, you can swap out older technology for newer ones. You can also expand or downsize your physical security architecture as your needs evolve, or choose to upgrade one site at a time.
Here are 4 ways open architecture can benefit your organization:
- Work with your preferred channel partner to procure and service your access control deployment, gaining access to a roster of integrators and expert advice
- Have the freedom to choose your software and hardware devices such as controllers, locks, and sensors
- Get in on new access control technology including mobile credentials, biometric readers, smart management solutions, and more
- Take control of your system and swap out technologies or providers as needed without any rip-and-replace scenarios
BLOG
Getting the ultimate flexibility of the cloud
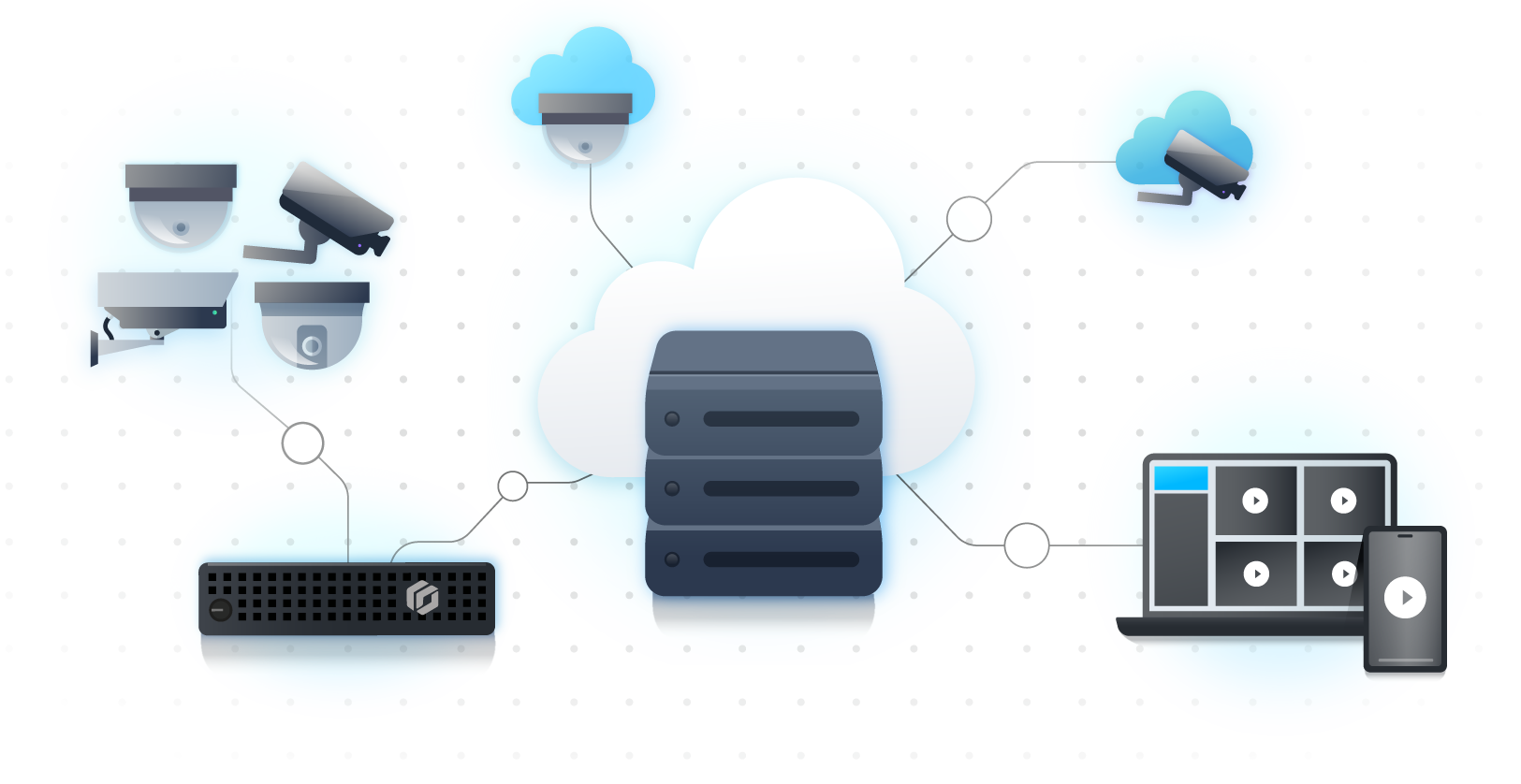
If a higher level of flexibility matters to you, there’s one more consideration in your access control decision that can go a long way: considering access control as a service (ACaaS).
ACaaS is a cloud-native access control solution that’s delivered as a subscription-based service by your technology provider. Open architecture ACaaS means you can easily upgrade existing deployments using cloud-managed intelligent controllers and appliances. This helps you keep and connect existing access control readers while opening you up to various other vendors’ technology. Choosing an open and unified ACaaS solution helps create a simpler deployment infrastructure without limitations, where you can upgrade sites at your own pace.
A hybrid-cloud deployment can help you get the best of both worlds. All on-premises and cloud-connected sites can stream back into one unified platform. So no matter where you’re located, you can easily manage events, credentials, and cardholders across your organization.
BLOG
Choosing between proprietary and non-proprietary
Our world is becoming increasingly interconnected, and so are access control systems. Organizations are prioritizing flexible, adaptable, and user-friendly physical security solutions that can evolve with their needs. Whether your organization is growing or adding new applications to your infrastructure, migrating to an open, non-proprietary, and unified access control solution allows you to adapt to future changes.
