Why unification is your best path forward
The pros and challenges of integrated and unified physical security systems.

Bringing all your physical security systems together is a step towards greater efficiency and cost savings. But you might be wondering if you should integrate your systems, use unification as a first step and then add other integrated solutions later, or unify everything together under one user interface (UI). Keep reading to find out which one is right for your organization.
GUIDE
Option#1: An integrated physical security system
An integrated physical security system connects multiple security components—such as video surveillance, access control, and intrusion detection—using middleware or APIs. While this approach allows different security systems to communicate, it often involves separate user interfaces and management tools, leading to potential inefficiencies.
Pros of an integrated system:
- Allows organizations to leverage existing security investments without replacing entire systems.
- Provides flexibility to add best-in-class solutions from different vendors.
- Can be a cost-effective initial approach, avoiding the need for a complete system overhaul.
Challenges of an integrated system:
- Operators must manage multiple user interfaces, leading to inefficiencies and longer response times.
- Compatibility issues can arise when connecting legacy systems with newer technologies.
- Cybersecurity risks increase, as vulnerabilities in one system can impact others.
- As security needs evolve, scaling and maintaining integrations may become complex and expensive.
Many organizations begin with integration but eventually face limitations in data-sharing, response coordination, and user efficiency. This is where unification comes into play.
BLOG
Option #2: A blend of both integrated and unified physical security
Many organizations take a combined approach, blending both integrated and unified security solutions. This allows them to unify their most critical systems while integrating third-party solutions as needed. By adopting this flexible strategy, organizations can balance cost, functionality, and long-term scalability.
BLOG
Pros of a blend of unified and integrated security approach:
- Best of both worlds: Organizations can unify core security functions while integrating specialized third-party solutions.
- Gradual transition: Companies can start with integration and progressively move toward a fully unified system at their own pace.
- Vendor flexibility: Businesses aren’t locked into a single ecosystem and can leverage the latest advancements in third-party security technology.
- Scalability and adaptability: The ability to integrate new technologies over time allows organizations to stay agile and responsive to evolving threats.
Challenges of a blend of unified and integrated security approach:
- Complexity in system management: Operators may still need to navigate multiple user interfaces, reducing efficiency compared to a fully unified system.
- Cybersecurity concerns: Weaknesses in integrated third-party solutions could introduce vulnerabilities into the unified platform.
- Higher maintenance costs: Managing both unified and integrated systems may require additional IT resources and ongoing maintenance.
- Data silos: While some security components are unified, other integrated solutions may not share data as seamlessly, limiting overall system intelligence.
A hybrid approach offers flexibility, but it also requires careful planning to ensure seamless interoperability and cybersecurity protection. Organizations that standardize on open-architecture solutions and prioritize strong vendor partnerships will be best positioned for long-term success.
BLOG
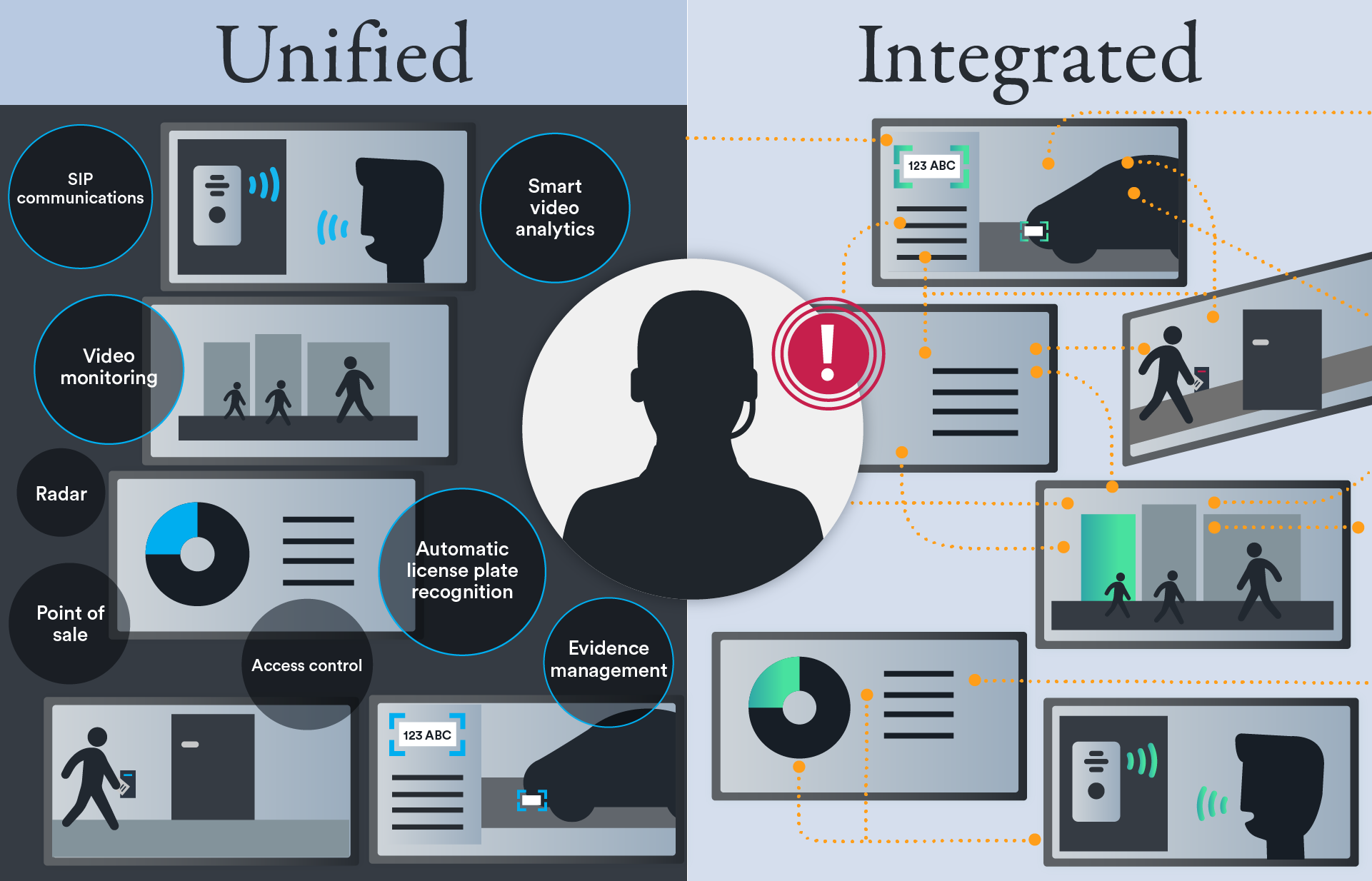
Option #3: Unified from start to finish
A fully unified physical security system is built on a single platform, seamlessly connecting video surveillance, access control, automatic license plate recognition (ALPR), intrusion detection, intercoms, and other security tools. Unlike integration, unification ensures that all components work together under one user interface, offering a seamless experience for operators.
A unified physical security solution allows you to choose from an expansive list of technology partners and solutions. You can even customize and build connections to existing devices and systems, expanding the scope of functionality and data available within your solution.
Integration can be complementary to unification. But to achieve that, you need strong integrations within a rich, open, and unified platform to extract the most value from your investments.
FREE EBOOK
Benefits of full unification:
- Single user interface: Operators can manage all security functions from one centralized dashboard, improving situational awareness and response times.
- Stronger cybersecurity: A unified platform reduces potential security gaps caused by incompatible third-party integrations.
- Lower total cost of ownership: Organizations save on maintenance, training, and licensing fees compared to managing multiple integrated solutions.
- Improved data correlation: A unified system can analyze and correlate data across all security functions, providing valuable insights for proactive decision-making.
- Scalability: As security needs grow, a unified platform allows for easy expansion without complex integrations.
For organizations prioritizing long-term efficiency, cybersecurity, and ease of use, unification from the start is often the best strategy. It eliminates the inefficiencies of integration while providing a foundation for evolving security needs.
BLOG
Real-world applications and benefits
Here are some practical advantages of unified physical security across various sectors:
Airports |
Unified solutions can feed comprehensive security data into analytics software, offering insights into terminal usage, density, and traveler flow. This enables Airport management to take actions that reduce wait times and enhance passenger experiences.
Retail |
Customer intelligence gathered through unified systems facilitates visitor counting, conversion rate analysis, queue management, and heat mapping. Retailers can leverage this data to better understand consumer behavior, make informed decisions, and boost in-store profitability.
Education |
Schools benefit from unification by integrating video surveillance, access control, and emergency response systems. A single platform ensures rapid lockdown procedures and improved student and staff safety.
Public safety |
Emergency responders and law enforcement agencies can unify video surveillance, dispatch systems, and situational awareness tools to improve response times and coordination during crises. Real-time data sharing enhances decision-making in critical incidents.
Government |
Municipalities and government agencies can integrate security across offices, public spaces, and infrastructure to improve access control, cybersecurity, and compliance with regulatory requirements. A unified system helps manage risks while enhancing operational efficiency.
Law Enforcement |
Police departments can unify real-time video surveillance, body camera footage, license plate recognition, and emergency dispatch systems. This enhances investigations, streamlines incident response, and improves collaboration between agencies.
Gaming and casinos |
Casinos must comply with strict security and regulatory requirements. A unified security system provides seamless monitoring of gaming floors, entrances, and back-office operations while ensuring compliance with industry regulations.
Financial institutions |
Banks and financial service providers use unified systems to manage access control, video monitoring, and fraud prevention across branches and ATMs. Centralized data analysis enhances security while ensuring compliance with banking regulations.
Data centers |
Cybersecurity meets physical security in data centers, where unified solutions integrate intrusion detection, biometric access, and environmental monitoring to protect critical infrastructure.
Transit systems |
Unification enables real-time monitoring of public transportation networks, integrating fare collection, video surveillance, and emergency response. Transit agencies can use data insights to enhance passenger safety, reduce delays, and improve overall service efficiency.
Smart cities |
Cities can leverage unified security platforms to connect traffic management, public surveillance, and emergency services. This helps optimize traffic flow, reduce crime, and enhance urban planning with data-driven decision-making.
Corporate campuses |
Corporate headquarters can unify access control, visitor management, and security monitoring across multiple locations. This helps streamline operations, enhance employee safety, and reduce operational costs.
Sports venues and stadiums |
Large-scale venues hosting sporting events and concerts can benefit from unified security platforms that combine crowd monitoring, ticket validation, emergency response, and perimeter surveillance. This enhances fan safety, optimizes staffing, and ensures compliance with event security regulations.