Id-Gate – Facial Recognition Software for ACS
RecFaces’ Id-Gate is a facial recognition software product for biometric identity verification in access control and management systems.
It enables organizations to enhance existing ACS solutions with biometric capabilities without requiring significant additional investment.
Supported features :
- Facial Recognition Analytics
- Real-Time Access Control with Genetec Event Triggering
- Bi-Directorial Profile Synchronization
- Liveness Detection to prevent spoofing attempts using photos or videos
- Multi-Factor Authentication Support
Jump to
Industry
- Airports
- Energy Utilities
- Seaports
- Gaming
- Manufacturing Wholesale
- Data Centers
- Government
- Banking
- Cities
- Corporate Campuses
- Education
- Financial Institutions
- Healthcare
- Public Safety
- Retail
- Sports Entertainment
- Transit
Availability
- Americas
- Asia Pacific
- Australia And New Zealand
- Europe
- Middle East And Africa
Product line
- Security Center
Id-Gate Solution Overview
Id-Gate is a facial recognition software product for biometric identity verification in access control and management systems.
It enables organizations to enhance existing ACS solutions with biometric capabilities without requiring significant additional investment.
Main Features:
- Identification Mode
- Virtual Access Points
- Data Synchronization
- Facial Recognition Analytics
- Bi-Directorial Profile Synchronization
- Real-Time Access Control with Genetec Event Triggering
- Customizable Instant Notifications
- Advanced Reporting and Audit Trails
- Multi-Factor Authentication Support
- Liveness Detection to prevent spoofing attempts using photos or videos
Key Market Applications
Challenges:
- Unauthorized transfer of RFID cards to third parties
- Several individuals entering using the same pass card or someone’s photo or video recording
- Low throughput during peak hours, as individuals may take up to 10 seconds to locate their pass cards
- Lack of control over the passage of people in areas without actuators
Solutions:
- Facial biometrics verifies the identity of the cardholder within 1 second, comparing their face at the entrance and the one of cardholder. The access is denied to the impostor
- Facial recognition detects all the faces captured on camera, immediately notifying security about those people who enter without a card
- Biometric authentication allows entrance within 1 second, significantly improving throughput
- Liveness detection feature ensures that a person is physically present during facial recognition authentication, preventing spoofing attempts using static images or videos
- Camera-based access control eliminates the need for doors and turnstiles by accurately detecting all individuals within its field of view, given proper placement and focal length.
Features & Benefits
Id-Gate Facial Recognition Software can easily extend ACS capabilities without programming by adding the following features:
Identification Mode :
- Description: Utilizes a biometric attribute (facial recognition) as the sole method for contactless access confirmation.
- Benefit: Provides a secure and convenient way to verify identity without the need for physical access cards, PINs or additional authentication factors.
Virtual Access Points:
- Description: Records a person’s presence at specific locations with timestamps, creating a virtual checkpoint. Verifies the individual's access levels and rights to the location.
- Benefit:
- Enforces access control policies at each checkpoint
- Enables real-time personnel tracking within premises
- Provides insights into space utilization and workflow efficiency
Data Synchronization:
- Description: Ensure seamless data transfer between Id-Gate and Genetec Security Center, including commands, access events and object updates.
- Includes synchronization of:
- Profiles
- Cards
- Access Levels
- Locations
- Devices
Facial Recognition Analytics
- Description: Analyzes and tracks facial data to extract key insights into demographic patterns, behavior, and trends for security or operational optimization.
- Benefit:
- Enhances security by identifying unauthorized individuals
- Provides valuable insights into user behavior
- Improves operational efficiency by leveraging data-driven insights
Bi-Directorial Profile Synchronization
- Description: Synchronizes user profiles across multiple systems, ensuring data consistency and real-time updates both ways.
- Benefit:
- Reduces data discrepancies
- Ensures that user profile changes are reflected instantly across all connected platforms for improved security and convenience
Real-Time Access Control with Genetec Event Triggering
- Description: Enables immediate access control of physical and logical access, with Genetec Event Triggering enabling immediate response to events such as unauthorized access attempts or security breaches.
- Benefit:
- Enhances security by allowing for rapid responses to security events
- Improves monitoring of access activity
- Reduces the risk of unauthorized access in real time
Customizable Instant Notifications
- Description: Allows users to set personalized notifications based on specific triggers, such as access attempts, system health, or security breaches, delivered instantly via various communication channels.
- Benefit:
- Ensures timely responses to critical events
- Improves security awareness and operational control
Advanced Reporting and Audit Trails
- Description: Generates comprehensive, detailed reports and maintains an audit trail for all system activities, providing a transparent log of actions, access events, and system changes.
- Benefit:
- Improves compliance by providing detailed tracking and historical records
- Simplifies troubleshooting
- Enhances accountability and transparency in security management
Multi-Factor Authentication Support
- Description: Integrates additional layer of security, requiring users to provide multiple forms of identification (e.g., biometric data, PIN, or mobile device authentication) to verify access.
- Benefit:
- Strengthens security by ensuring that unauthorized individuals cannot gain access even if one authentication factor is compromised
- Provides greater protection for sensitive data and systems
Liveness Detection
- Description: Uses AI-driven technology to ensure that a person is physically present during facial recognition authentication, preventing spoofing attempts using static images or videos.
- Benefit:
- Increases the accuracy and reliability of facial recognition, ensuring that only live individuals gain access
- Reduces the risk of identity fraud and spoofing attacks
Deployment Options:
- Flexible Deployment Models: Available as on-premises, cloud-based, or hybrid solutions to meet diverse organizational needs.
Installation and Integration:
- Quick Setup: Plug & Play installation completed in just 20 minutes.
- Easy Integration: Seamless connection to existing Access Control Systems (ACS).
Security and Access Management:
- Multi-Factor Authentication (MFA): Enhances security with multiple authentication methods.
- Efficient Entry Management: Ensures smooth and efficient people flow at entrances.
- Convenient Guest Access: Simplifies access for visitors with easy management tools.
- Automatic Profile Updates: Keeps user profiles current without manual intervention.
System Control and Notifications:
- Compromise Control: Monitors and mitigates security threats.
- Flexible System Settings: Customizable system and notification settings to fit specific needs.
- Centralized Configuration: Manage all terminals from a single, centralized interface.
- Virtual Access Control Points: Utilize virtual checkpoints for enhanced access control.
Reporting and Compliance:
- Detailed Reporting: Generates comprehensive reports on access activities, including time and attendance tracking.
- GDPR Compliance: Ensures full compliance with the General Data Protection Regulation (GDPR).
Directory Integration:
- Directory Services Integration: Compatible with existing directory services such as Active Directory (AD), LDAP, and other identity providers.
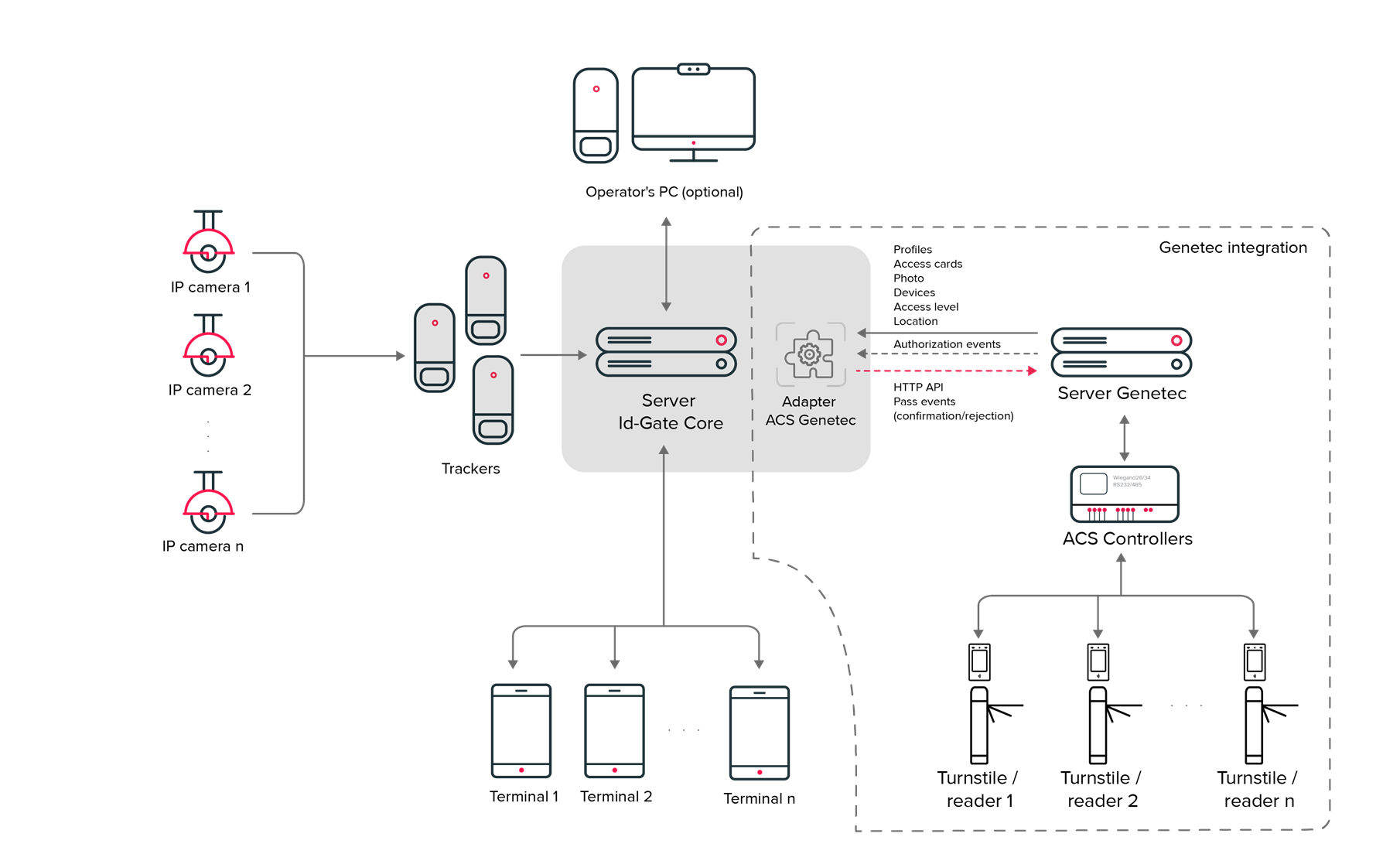
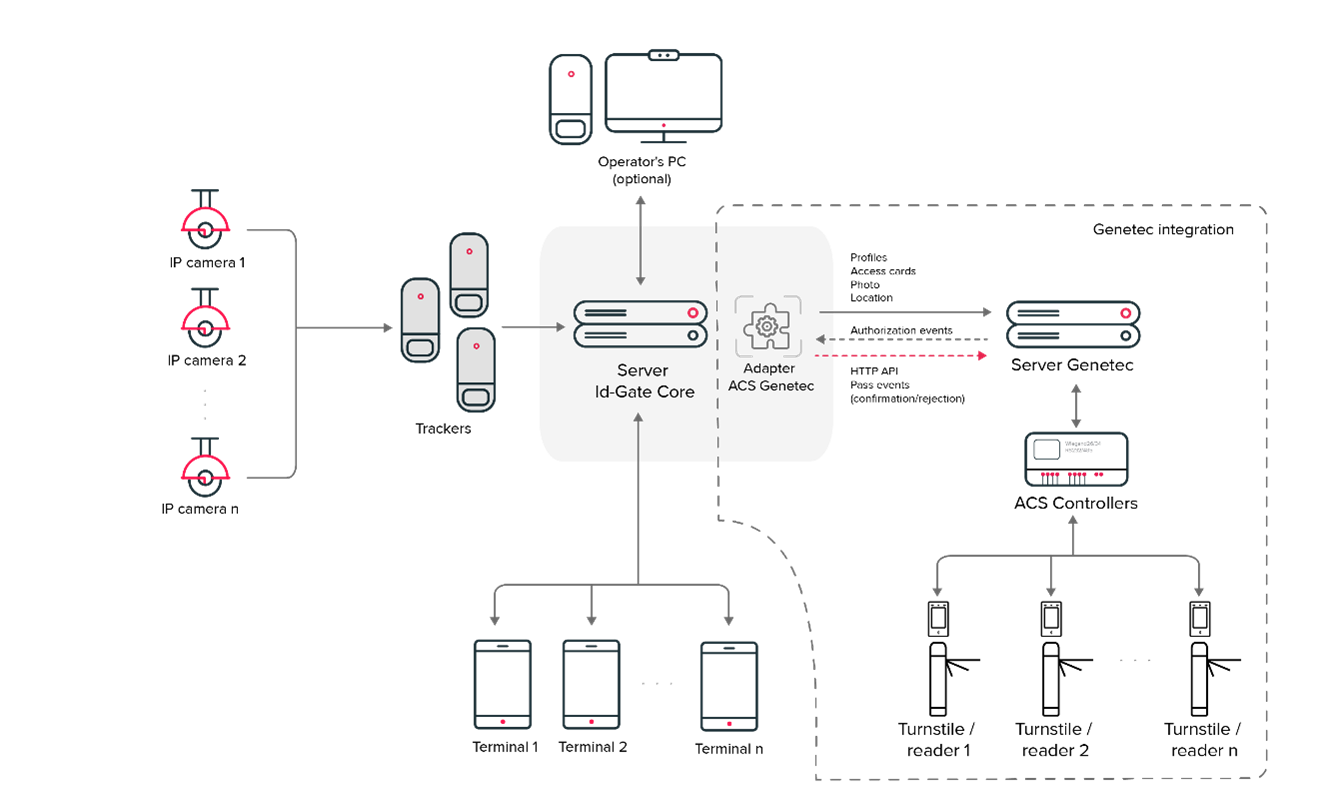
Solution Architecture
Key Components
- Genetec Security Center: The existing ACS platform that manages access policies, user profiles, and logs access events.
- IP cameras or biometric terminals: Installed at entry points to capture and verify the facial features of individuals.
- Id-Gate System: The central software that manages facial recognition module and integrates with the existing ACS.
There are two synchronization modes between Id-Gate and the Genetec Security Center:
Master — mode of one-way data reception FROM the Genetec Security Center (data from the Genetec Security Center are prioritized);
Slave — mode of one-way data sending TO the Genetec Security Center (data from Id-Gate system are prioritized) available for objects “Location”, “Photo”, “Profiles”, “Cards”.